GLOSSARY
What is Network Surveillance?
Surveillance threats can originate from actors who have gained access to foreign mobile networks located around the world. Network surveillance is made possible through a surveillance software platform that connects to a mobile network and sends signaling command messages commonly used for international roaming. Since the messages are used in mobile networks, they don’t require malware or software installed on a victim’s phone in order to extract information or intercept communications.
What is Maleware?
Malware is a collective term for any type of malicious software designed to infiltrate your device without your knowledge, cause damage and disruption, or steal data. Adware, spyware, viruses, botnets, trojans, worms, rootkits and ransomware all fall under this umbrella term.
What is Mobile Maleware?
Mobile malware is malicious software designed to target mobile devices with the goal of gaining access to private data. The growing threat of mobile malware to steal information goes beyond surveillance to crypto and financial theft, and accessing corporate networks from personal devices. Mobile malware can attempt to replicate itself from device to device and cause unpredictable behavior.
How to Stop Malware Threats?
Protecting yourself from surveillance malware requires prevention and taking an active role to reduce your risk. While protection cannot be guaranteed, there are techniques to help mitigate your exposure to these threats.
Keep your device updated
Google Android and Apple iPhone regularly release updates, and many of them are security-related. And while both provide notifications on the availability of updates, updates may be available before you receive the message so it’s important to manually check. If you have an Android device, check this Android Help Page. For iPhone devices, check Apple’s iOS page.
Keep your software updated – Malware is often distributed from device apps. It is therefore recommended to keep your apps updated by configuring your device to automatically update them or to regularly check for app updates. Web browsers and social media apps can be vulnerable.
What is Spyware?
Spyware is a type of malware that perform certain tasks include watching and tracking of user actions and collecting personal data. Spyware programs generally install themselves on user computer and provides profit to the third party by collecting data of user without his awareness. Moreover, spyware steal passwords and personal information of the users by running in background in the system.
Spyware Architecture:
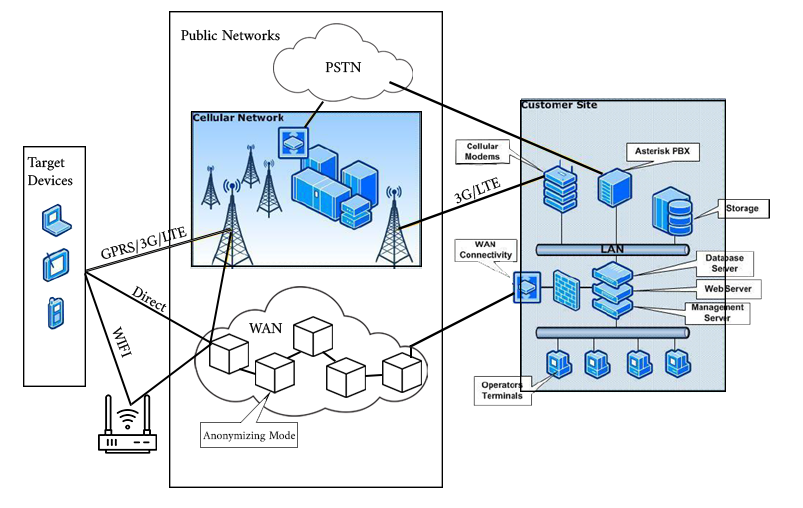
Types of Spyware:
Class A Spyware ( Pegasus, Predator , Graphite ) use zero-day full-chain to compromise targets.
Class B Spyware ( others ) use not patched vulnerabilities to compromise targets.
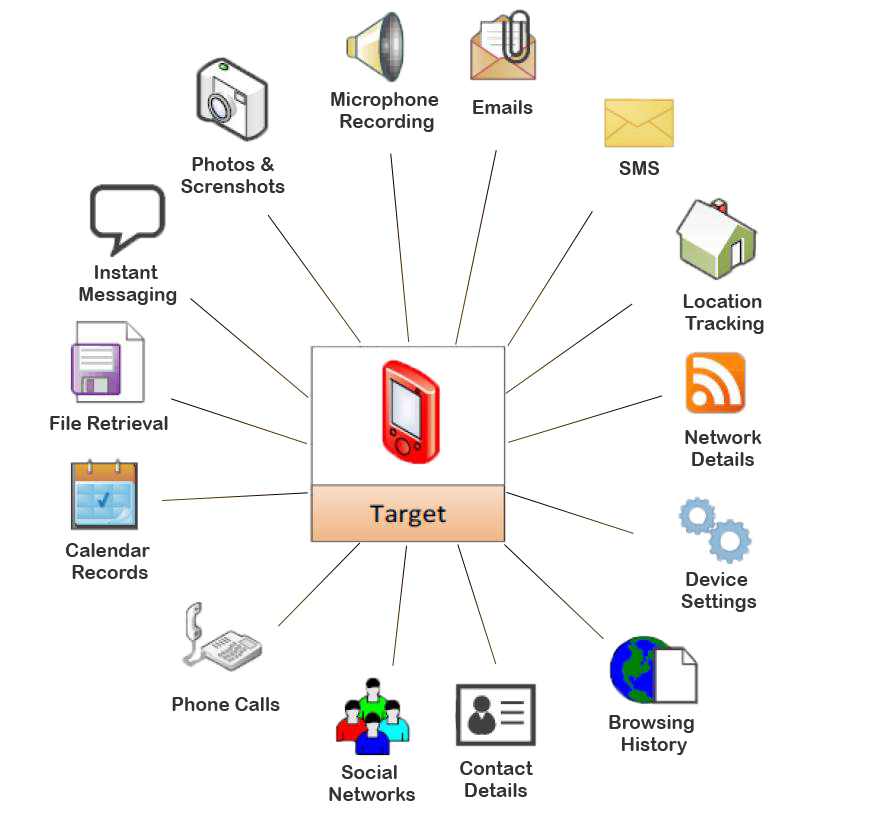
What data a Spyware collect?
See the below picture which explains best what Spyware is able to collect.
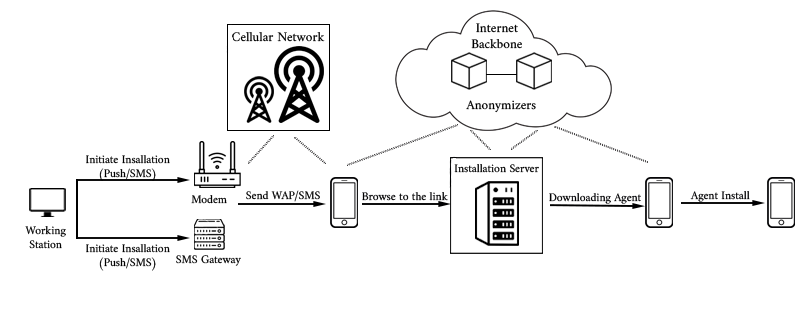
How Mobile Spyware are installed into targets?
See the below picture which explains best how Mobile Spyware are installed into targets:
How Spyware hide itsfelf?
Spyware use anonymouse backbone and TOR to hide itself in the network.
How do i can remove a Spyware?
Make a firmware update or a hard factory reset of your device.
Are there any phone that Spyware cannot compromise?
Yes, you can use our securephone with limited functionality.
What is a anonymous Backbone?
A backbone or core network is a part of a computer network which interconnects networks, providing a path for the exchange of information between different LANs or subnetworks. A backbone can tie together diverse networks in the same building, in different buildings in a campus environment, or over wide areas .
So Anonymous Backbone is a backbone to hide itself. This kind of backbone are used by last generations of spyware.

What is Information Disclosure?
In this type of attack, the bad actor is trying to gather information about the target phone in order to launch other attacks listed below. Generally speaking, this involves resolving a victim’s mobile phone number into their mobile network identity (IMSI) to discover if the phone is live on a mobile network in a particular country to conduct a surveillance operation.
What is a Trojan Horse?
Trojan Horse is also a type of malware which uses false and fake name for mislead users from its true intent and executing them. Trojan Horses generally install on the system as legitimate and useful software that can give unauthorized access and control of the system to the hackers. Back orifice, Rootkit and Beast Trojan are some of the common Trojan horse which is more harmful.
What is a Virus?
A Virus is a computer program or software that connect itself to another software or computer program to harm computer system. When the computer program runs attached with virus it perform some action such as deleting a file from the computer system. Virus can’t be controlled by remote.
What is Worms?
Worms is also a computer program like virus but it does not modify the program. It replicate itself more and more to cause slow down the computer system. Worms can be controlled by remote.
What is Ransomware?
Ransomware is a type of malware that is designed to block user access from own system until a ransom fee is paid to ransomware creator. Ransomware is a lot dangerous than a regular malware and spread through phishing emails having infected attachments. Ransomware has emerged over the last few years and can attack individuals or organizations.
What is a Rootkit?
Rootkit is a set of application, a type of maleware hat is designed to infect a target PC and allow an attacker to install a set of tools that grant him persistent remote access to the computer. The malware typically pretended itself as normal files that “hide in plain sight” so your antivirus software overlooks them. It enables administrator-level access to a computer or computer network. The motive is to steal the identity information from your computer, often to gain control of a system. It is difficult to detect and remove, requires the specialized tools to remove.
What is Scareware?
Scareware is a form of malware that is malicious software that poses as legitimate computer security software and claims to detect a variety of threats on the affected computer that do not actually exist. The users are then informed that they have to purchase the scareware in order to repair their computers and are barraged with aggressive and pop up notifications until they supply their credit card number and pay up the desired amount for the worthless scareware product.
What is a Trap door?
A trap door is kind of a secret entry point into a program that allows anyone to gain access to any system without going through the usual security access procedures.
Another definition of a trap door is it is a method of bypassing normal authentication methods. Therefore it is also known as a back door.
Trap Doors are quite difficult to detect and also in order to find them the programmers or the developers have to go through the components of the system.
What is vulnerability?
A vulnerability is a hole or a weakness in the application, which can be a design flaw or an implementation bug, that allows an attacker to cause harm to the stakeholders of an application. Stakeholders include the application owner, application users, and other entities that rely on the application.
See also: https://en.wikipedia.org/wiki/Common_Vulnerabilities_and_Exposures
What is 0day (zero-day)?
A zero-day is a computer-software vulnerability previously unknown to those who should be interested in its mitigation, like the vendor of the target software. Until the vulnerability is mitigated, hackers can exploit it to adversely affect programs, data, additional computers or a network.
See also: https://en.wikipedia.org/wiki/Zero-day_(computing)
Location discovery:
From the mobile network, a bad actor may be able to track a victim’s location down to the individual mobile cell site or even obtain GPS coordinates of the device without seeking permission from the network operators from which the information is extracted.
(c) 2024 Omnivisix Solutions GmbH